- How man in the middle attack violates the security?
- Why MITM attack is dangerous?
- What are possible safeguards against MITM attacks?
- How common are man in the middle attacks?
- What is the key requirement for a man in the middle attack to be successful?
- Does VPN protect against man in the middle attacks?
- Is man-in-the-middle passive attack?
- What are the types of man-in-the-middle MITM attacks?
- Is SSL vulnerable to man-in-the-middle?
- How can malware attacks be prevented?
- Can SSL protect against MitB?
- How can DoS attacks be prevented?
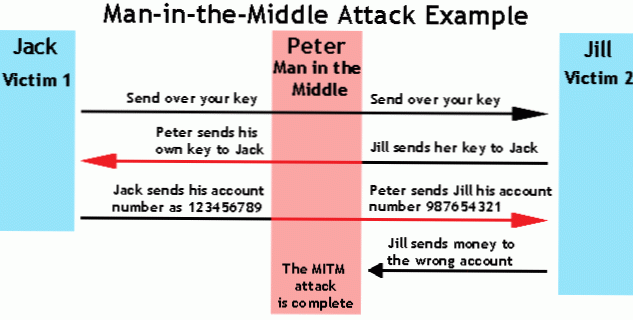
How man in the middle attack violates the security?
A man-in-the-middle attack is a type of eavesdropping attack, where attackers interrupt an existing conversation or data transfer. After inserting themselves in the "middle" of the transfer, the attackers pretend to be both legitimate participants.
Why MITM attack is dangerous?
Why are MitM hacks so dangerous? ... In addition, threat actors could use Man-in-the-Middle attacks to harvest personal information or login credentials. Further, attackers could force compromised updates that install malware can be sent on users' mobile devices instead of legitimate ones.
What are possible safeguards against MITM attacks?
SSL Hijacking, SSL Stripping and HTTPS Spoofing are some of the common ways attackers deploy to steal information from innocent users. Using secure private networks, using HTTPS and strengthening security measures are the options left for users to protect themselves from MITM attacks.
How common are man in the middle attacks?
Though not as common as ransomware or phishing attacks, MitM attacks are an ever-present threat for organizations. IBM X-Force's Threat Intelligence Index 2018 says that 35 percent of exploitation activity involved attackers attempting to conduct MitM attacks, but hard numbers are difficult to come by.
What is the key requirement for a man in the middle attack to be successful?
The attacker must be able to intercept all relevant messages passing between the two victims and inject new ones. This is straightforward in many circumstances; for example, an attacker within the reception range of an unencrypted Wi-Fi access point could insert themselves as a man-in-the-middle.
Does VPN protect against man in the middle attacks?
Using a VPN disguises the user's IP address and country location to bypass geo-blocking and internet censorship. VPN is also effective against man-in-the-middle attacks and for protecting online cryptocurrency transactions.
Is man-in-the-middle passive attack?
Types of Man-in-the-Middle Attacks
Wi-Fi Eavesdropping – a passive way to deploy MITM attacks, Wi-Fi eavesdropping involves cyber hackers setting up public Wi-Fi connections, typically with an unsuspecting name, and gain access to their victims as soon as they connect to the malicious Wi-Fi.
What are the types of man-in-the-middle MITM attacks?
MitM Attack Techniques and Types
- ARP Cache Poisoning. Address Resolution Protocol (ARP) is a low-level process that translates the machine address (MAC) to the IP address on the local network. ...
- DNS Cache Poisoning. ...
- HTTPS Spoofing. ...
- Wi-Fi Eavesdropping. ...
- Session Hijacking.
Is SSL vulnerable to man-in-the-middle?
The structure of an SSL Certificate makes Man-in-the-Middle intrusive activity impossible. These web security products have been specifically designed to protect websites and customers from this type of cyber attacks.
How can malware attacks be prevented?
Let's look into the best ways to stop a malware attack.
- Keep an eye out for phishing emails. In order to gain network access, threat actors need to have a starting point. ...
- Odd logins. ...
- Backdoor Trojans. ...
- Information on the Move. ...
- Data Compression and Exporting. ...
- Malware prevention: Protect your company.
Can SSL protect against MitB?
Man-in-the-browser attacks can defraud even the most vigilant users and are immune to some well-known security mechanisms like secure SSL/TLS certificates and two-factor authentication. ... Hence, no authentication step has been bypassed. MitB trojan modifies the data before it gets encrypted.
How can DoS attacks be prevented?
How to help mitigate against DoS attacks and DDoS attacks
- Keep your security software, operating system, and applications updated. ...
- Consider a router that comes with built-in DDoS protection.
- Look for a website hosting service with an emphasis on security.
 Usbforwindows
Usbforwindows
![How do i create a an upvoting system like that of producthunt or coinhunt? [closed]](https://usbforwindows.com/storage/img/images_1/how_do_i_create_a_an_upvoting_system_like_that_of_producthunt_or_coinhunt_closed.png)